This report reviews an ongoing cyber-attack campaign dating back to mid-2014. Additional sources indicate it may date as far back as 2011. We call this campaign Thamar Reservoir, named after one of the targets, Thamar E. Gindin, who exposed new information about the attack and is currently assisting with the investigation.
The campaign includes several different attacks with the aim of taking over the target’s computer or gain access to their email account. We estimate that this access is used for espionage or other nation-state interests, and not for monetary gain or hacktivism. In some cases, the victim is not the final target; the attackers use the infected computer, email, or stolen credentials as a platform to further attack their intended target.
The attackers are extremely persistent in their attempts to breach their targets. These attempts include:
- Breaching trusted websites to set up fake pages
- Multi-stage malware
- Multiple spear phishing emails based on reconnaissance and information gathering.
- Phone calls to the target.
- Messages on social networks.
While very successful in their attacks – the attackers are clearly not technically sophisticated. They are not new to hacking, but do make various mistakes – such as grammatical errors, exposure of attack infrastructure, easy to bypass anti analysis techniques, lack of code obfuscation, and more.
These mistakes enabled us to learn about their infrastructure and methods. More importantly, we have learned of 550 targets, most of them in the Middle East, from various fields: research about diplomacy, Middle East and Iran, international relations, and other fields; Defense and security; Journalism and human rights; and more.
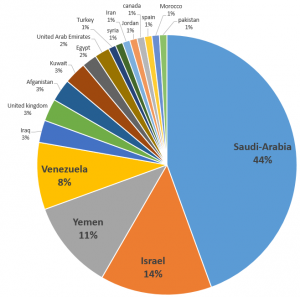
Below is the target distribution by country (click the image for full size):
Various characteristics of the attacks and their targets bring us to the conclusion that the threat actors are Iranian. In addition, we note that these attacks share characteristics with previously documented activities:
- Attacks conducted using the Gholee malware, which we discovered.
- Attacks reported by Trend Micro in Operation Woolen-Goldfish.
- Attacks conducted by the Ajax Security Team as documented by FireEye.
- Attacks seen during Newscaster as documented by iSight.
Read the full report: Thamar Reservoir – An Iranian cyber-attack campaign against targets in the Middle East