 Earlier today the Israel Defense Forces (IDF) uncovered a campaign they attribute to Hamas, in which fake Facebook profiles were used to lure soldiers to install Android malware. ClearSky has been monitoring this campaign and would like to share indicators related to it.
Earlier today the Israel Defense Forces (IDF) uncovered a campaign they attribute to Hamas, in which fake Facebook profiles were used to lure soldiers to install Android malware. ClearSky has been monitoring this campaign and would like to share indicators related to it.
We were unable to find technical similarities or infrastructure overlap with a known threat actor.
However, we assess with medium certainty that the threat actor behind this campaign is Arid Viper based on the targeting of Israeli soldiers, type and character of fake personas on Facebook, and previous Arid Viper activity.
In 2017, the IDF published a report attributing a cyber campaign to Hamas. The campaign was similar to the current one, and revolved around multiple fake Facebook profiles that contacted Israeli Soldiers and induced them to install android malware. Two weeks later, Kaspersky published a technical report about this campaign (the Kaspersky report did not mention Arid Viper, however, it was later found related).
Indicators of compromise
These and other indicators of compromise are available for subscribers of the ClearSky threat intelligence service in MISP events: 771, 817, 814, 828.
goldncup[.]com
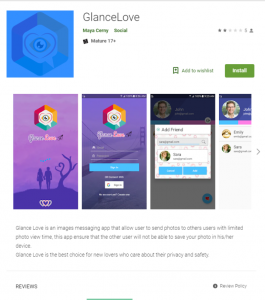
glancelove[.]com
autoandroidup[.]website
mobilestoreupdate[.]website
updatemobapp[.]website
com.winkchat.apk
com.coder.glancelove.apk
anew.football.cup.world.com.worldcup.apk
4f9383ae4d0285aeb86e56797f3193f7
95a782bd8711ac14ad76b068767515d7
b3e40659ae0a0852e2f6eb928d402d9d
f6ffa064a492e91854d35e7f225b1313
8f1b709ae4fb41b32674ca8c41bfcbf7
5b2aac6372dea167c737b0036e1bd515
7a9503152b4c8c1ee80ac7daf5405a91